


We are a digital agency helping businesses develop immersive, engaging, and user-focused web, app, and software solutions.
2310 Mira Vista Ave
Montrose, CA 91020
2500+ reviews based on client feedback
What's Included?
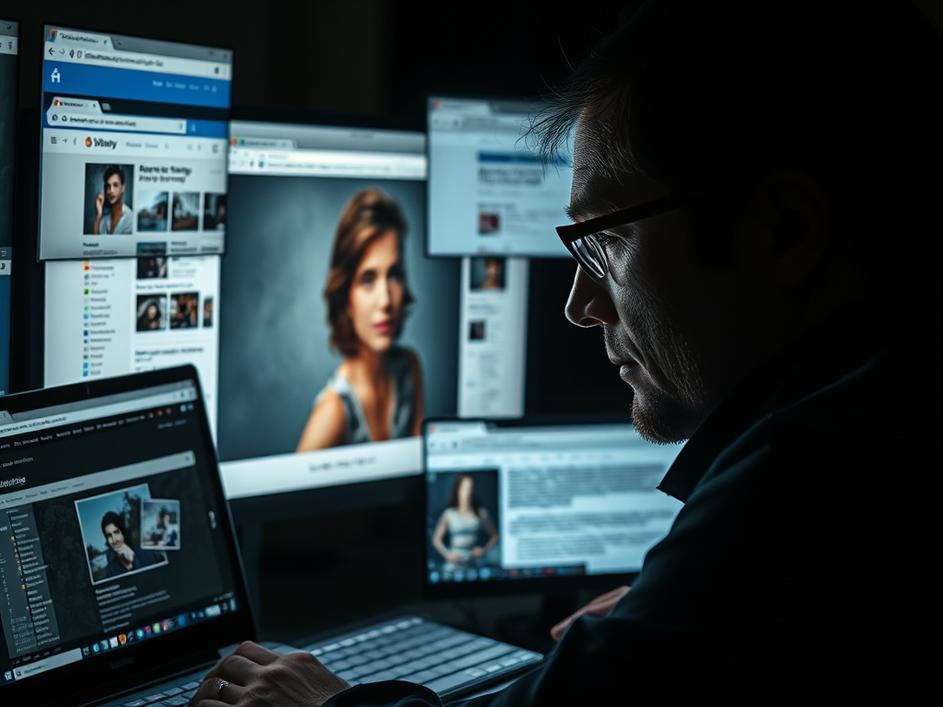
ToggleIn today’s hyper-connected world, images are everywhere. They’re shared on social media, embedded in websites, and sent through messaging apps. But what if a picture could tell you more than what’s immediately visible? What if you could use an image to uncover hidden information about its origin, its subject, or even the person who posted it? This is the realm of image-based Open Source Intelligence (OSINT), and it’s surprisingly accessible thanks to a range of free tools.
While the term “hacker” often conjures up images of shadowy figures breaking into computer systems, the reality is that many hackers are simply skilled researchers who use their knowledge to find vulnerabilities and expose information. In the context of OSINT, these individuals often employ a variety of techniques to track down details hidden within or associated with images. Understanding these techniques – and the tools they use – is crucial for anyone interested in digital investigations, whether you’re a journalist, a security professional, or simply someone who wants to be more aware of their online footprint. It’s important to emphasize that using these tools ethically and legally is paramount; avoid any activity that could be considered stalking, harassment, or a violation of privacy.
One of the most fundamental techniques in image-based OSINT is reverse image search. This involves uploading an image to a search engine like Google Images, TinEye, or Yandex Images, and asking the engine to find other instances of that image online. This can reveal where the image has been published, who has shared it, and even provide clues about its origin. Different search engines use different algorithms, so it’s often beneficial to try multiple engines for the same image. For example, Yandex Images is known for its ability to identify faces and objects within images, which can be useful for identifying individuals or landmarks.
Images often contain embedded metadata, also known as EXIF data, which can reveal a wealth of information about the image. This metadata can include the date and time the image was taken, the GPS coordinates of where it was taken, the camera model used, and even the name of the photographer. Tools like ExifTool (a command-line application) and online EXIF viewers can be used to extract this metadata. Analyzing this data can provide valuable clues about the image’s origin and context. However, it’s important to note that metadata can be easily modified or removed, so its absence doesn’t necessarily mean that no information exists.
Beyond reverse image search and metadata extraction, there are a number of more advanced techniques that can be used to investigate images. These include: Facial recognition: Using facial recognition software to identify individuals in images. Object recognition: Identifying objects and landmarks within images to determine their location or context. Image forensics: Analyzing the image for signs of manipulation or tampering. Geolocation: Using clues within the image, such as landmarks, signs, or foliage, to determine the location where it was taken. Many specialized tools are available for these tasks, some free and some paid. Keep in mind that the accuracy and reliability of these tools can vary, so it’s important to verify any findings using multiple sources.
It’s crucial to emphasize the ethical considerations involved in image-based OSINT. While these tools can be powerful for research and investigation, they can also be misused for malicious purposes. It’s essential to respect privacy, avoid stalking or harassment, and comply with all applicable laws and regulations. Always consider the potential impact of your actions and ensure that you are using these tools responsibly. Remember that just because information is publicly available doesn’t mean it’s ethical or legal to access or use it in a particular way.
The world of OSINT is constantly evolving, with new tools and techniques emerging all the time. It’s important to stay informed about the latest developments and to continuously update your skills. Follow OSINT experts on social media, attend conferences and workshops, and experiment with new tools and techniques. The more you learn, the more effective you’ll be at uncovering hidden information and protecting yourself from potential threats.
Image-based OSINT offers a powerful set of tools and techniques for uncovering hidden information in the digital world. By understanding how these tools work and how they can be used, you can empower yourself to conduct effective investigations, protect your privacy, and stay informed about the ever-evolving landscape of online security. However, remember that with great power comes great responsibility. Always use these tools ethically and legally, and always respect the privacy of others.


Comments are closed